Kubernetes Security Best Practices
A step-by-step checklist to secure Kubernetes clusters for reliable service offering.
Kubernetes has become the de facto operating system of the cloud. However, Kubernetes can be challenging to operate. Teams often put off addressing security processes until they are ready to deploy code into production.
Kubernetes requires a new approach to security earlier in the development cycle. Doing it later in the development life cycle slows down the pace of cloud adoption, while raising security and compliance risks.
This Kubernetes Security Guide is designed to give you the information you need to implement Kubernetes security and container security at scale. You’ll get a deeper understanding of:
- Securing container images in a CI/CD pipeline
- Securing the Kubernetes Control Plane
- Reducing risk with Role-Based Access Control
- Securing Pods with Pod Security Policies
- Securing cloud-native workloads at runtime
When addressing Kubernetes security, it is nearly impossible to separate the Kubernetes cluster from the other layers of cloud computing. These layers include the application or code itself, the container image, the Kubernetes cluster, and the cloud or networking layer as shown in the image below. Each layer builds on the previous layer, and all layers must be secured to achieve defense in depth.
Cloud Native Security Layers
Kubernetes Security Issues and DevOps
Another way to think more specifically about Kubernetes security from a developer point of view is to look at it across three distinct stages of the DevOps pipeline:
- Creating the container image during the build
- Configuring the Kubernetes infrastructure during deployment
- Securing network communication in production
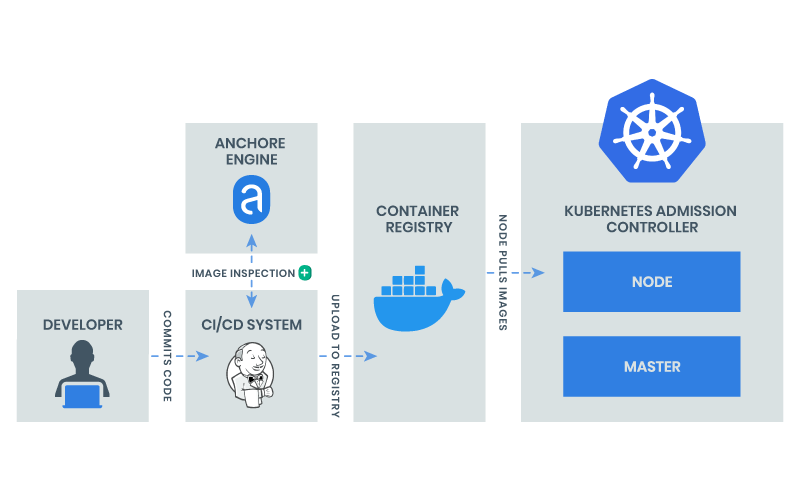
Ensure That Images Are Free of Vulnerabilities
Implement Continuous Security Vulnerability Scanning
Regularly Apply Security Updates to Your Environment
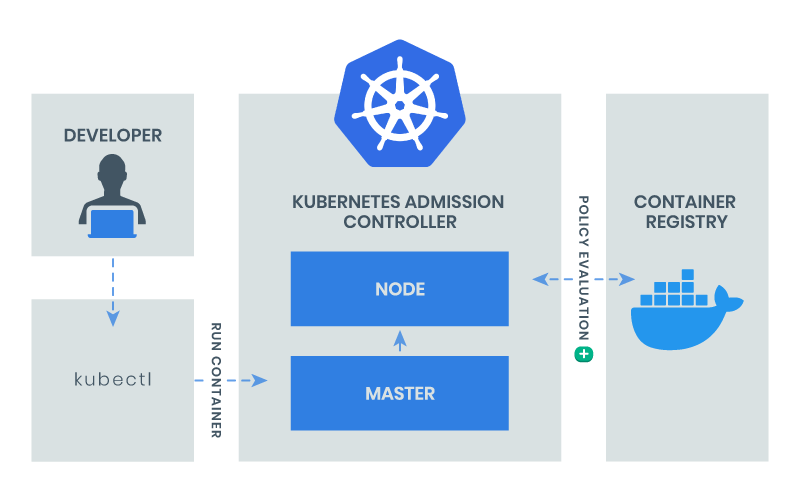
Enforce admission policies
Ensure That Only Authorized Images are Used in Your Environment
Limit Direct Access to Kubernetes Nodes
Create Administrative Boundaries between Resources
Define Resource Quota
Implement Network Segmentation
Apply Security Context to Your Pods and Containers
Log Everything
Upgrade to the latest version
Enable Role-Based Access Control (RBAC)
Use Namespaces to Establish Security Boundaries
Separate Sensitive Workloads
Run a Cluster-wide Pod Security Policy
Harden Node Security
Turn on Audit Logging
USE POLICIES TO GOVERN DEPLOYMENT
Network Policy

The DevOps Bootcamp 🚀 Newsletter
Join the newsletter to receive the latest updates in your inbox.




